Security Markets: The Lay of the Land | Summary and Q&A
TL;DR
Software's increasing presence in everyday objects presents challenges to the security industry, but improvements in device security and changes in threat landscape offer hope for the future.
Key Insights
- 🫚 The security industry has often focused on next-generation products rather than addressing root causes of breaches.
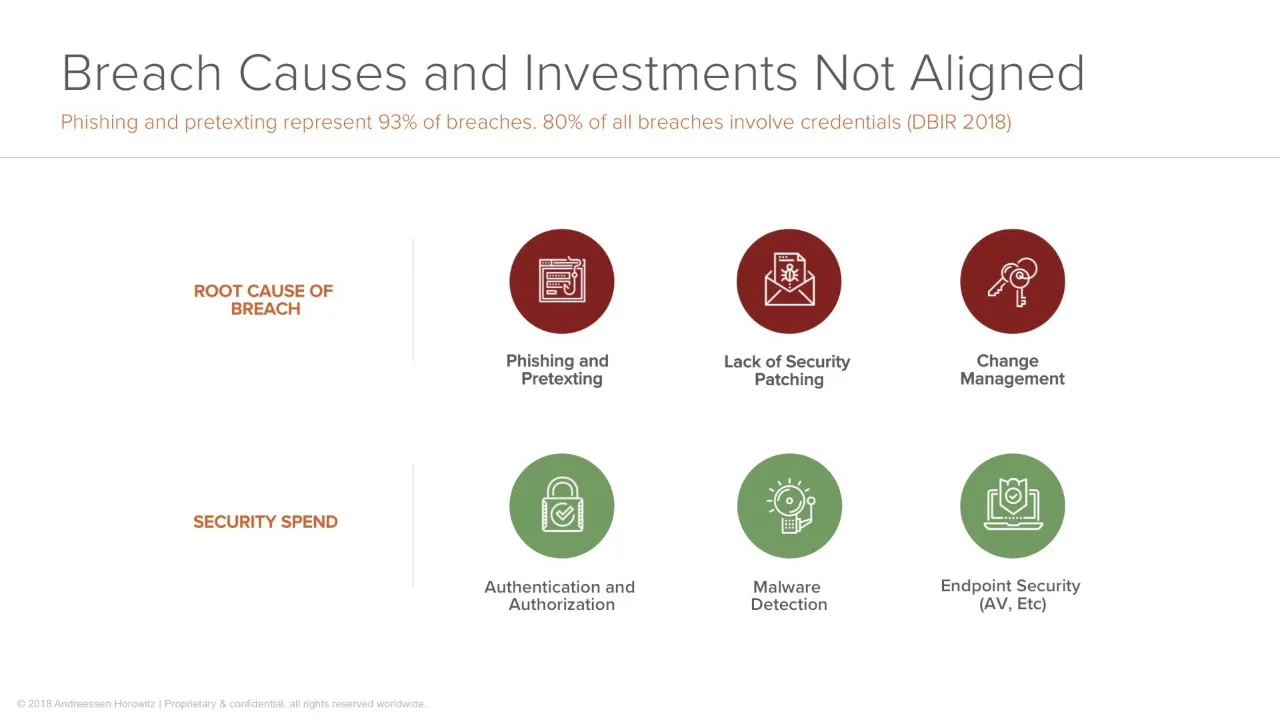
- 🖤 Fishing and pretexting, lack of security patching, and poor change management are major causes of breaches, with nation-state attacks being less prevalent.
- 😶🌫️ Cloud service providers and standards-based compliance are driving positive changes in security.
- 🔒 Blockchain technology has the potential to revolutionize security processes, particularly in areas like threat intelligence sharing.
Transcript
Read and summarize the transcript of this video on Glasp Reader (beta).
Questions & Answers
Q: What is the concept of "software eating the world" and why is it significant?
"Software eating the world" refers to the integration of software into previously hardware-based objects. This trend has increased the complexity and security challenges faced by the security industry.
Q: How has the security industry itself been a challenge to making things more secure?
The security industry has had misaligned incentives, with some cottage industries actually benefiting from breaking security models. Additionally, relying on software security to secure fundamentally insecure products has been problematic.
Q: What are some positive trends in device security?
Many devices now come with built-in security features. For example, Apple's iOS devices and Google's Chromebook have advanced security capabilities, improving overall device security.
Q: How have adversaries changed the security landscape?
E-crime syndicates have begun using cryptocurrency applications for attacks, such as mining cryptocurrencies using access to large cloud platforms. Ransomware attacks have also become more targeted, customized for specific victims.
Summary
This video discusses various trends and challenges in the field of software security. The speaker mentions how software is now integrated into everyday objects, and how the security industry itself can sometimes hinder rather than enhance security. He goes on to talk about the emerging trends in technology, such as built-in security features in devices and the use of blockchain technology. He also highlights the current challenges in cloud configuration and change control. Finally, he addresses the state of security spending and the importance of addressing the root causes of breaches.
Questions & Answers
Q: What is the concept of "software eating the world"?
"Software eating the world" refers to the idea that everything that used to exist solely in the hardware-based world is now running on software. Everyday objects like refrigerators and televisions now have some kind of code built into them.
Q: How has the security industry been problematic?
The security industry has often worked against making things more secure. There are misaligned incentives and cottage industries within the industry that actually benefit from breaking security models. This culture of hacking for profit has led to problematic developments in the security world.
Q: What changes are happening in terms of security in technology?
Two major trends are driving changes in technology: built-in security features in devices and the use of blockchain technology. Companies like Apple and Google have integrated security capabilities into their devices, and blockchain technology allows for building communities of interests that can work together and be compensated for their engagement.
Q: How have the adversaries in the security space changed?
Adversaries have shifted towards using cryptocurrency applications, leading to breaches where attackers gain access to cloud platforms to mine cryptocurrencies. Ransomware attacks have also become more targeted and sophisticated.
Q: What are some challenges in cloud configuration and change control?
Cloud configuration has become a real problem, as seen in cases where misconfigured permissions on cloud buckets led to data breaches. Change control in cloud environments has become increasingly challenging, as people make mistakes or accidentally check credentials into public repositories.
Q: How does the speaker characterize the state of security?
The speaker describes the state of security as both "fine" and "on fire." While there is more awareness and investment in cyber security, breaches are still occurring at a high rate. The speaker also mentions that most breaches are caused by simple human errors like phishing and lack of security patching.
Q: What are the main areas where security spending is focused?
Authentication and authorization systems, followed closely by malware detection and endpoint security solutions, dominate security spending. However, these areas do not necessarily address the root causes of breaches like patch management and change control.
Q: What are the main challenges for CISOs?
Finding and hiring security talent continues to be a significant challenge for CISOs. It can take months to find a junior level security engineer, and CISO searches often take over a year. Additionally, CISOs face the frustration of inadequate security tools and a lack of time and resources to explore new technologies.
Q: What is the role of standards-based compliance in driving change in security?
Standards-based compliance, such as the NIST 853 standard and the FedRAMP process, has forced cloud service providers to internalize security. This has made them more transparent about their operations and has helped elevate the overall security ecosystem. The speaker predicts that the development of more meaningful standards and better certification processes will continue.
Q: How is blockchain technology viewed from a security perspective?
From a security perspective, blockchain technology is seen as a way to build communities of interests and create a more secure environment. It allows for compensation based on contributions to the network and provides a vetting mechanism. This could potentially improve threat intelligence sharing and other security activities.
Q: What does the speaker see in the future of security, five to ten years out?
The speaker envisions that cloud computing will dominate, with data centers being used primarily for secrets management infrastructure. Purpose-built devices will play a significant role and minimize the need for traditional bolt-on security measures. Additionally, he mentions the importance of the "beyond corp" and "zero trust" movements that eliminate implicit trust relationships on corporate networks.
Takeaways
In summary, software security faces various challenges and trends. The integration of software into everyday objects and the problematic nature of the security industry contribute to these challenges. However, there are positive developments, such as built-in security features in devices and the adoption of blockchain technology. Cloud configuration and change control are significant challenges, but standards-based compliance and improved risk management processes can drive positive change. The speaker also emphasizes the need to focus on addressing root causes of breaches, rather than solely relying on authentication and malware detection. Finally, the speaker envisions a future where cloud computing dominates, purpose-built devices play a major role, and security is based on principles like "beyond corp" and "zero trust."
Summary & Key Takeaways
-
Software has become pervasive in everyday objects, requiring security professionals to adapt to new challenges.
-
The security industry itself has often worked against making things more secure, creating misaligned incentives.
-
The emergence of secure devices and changes in the threat landscape offer potential solutions.